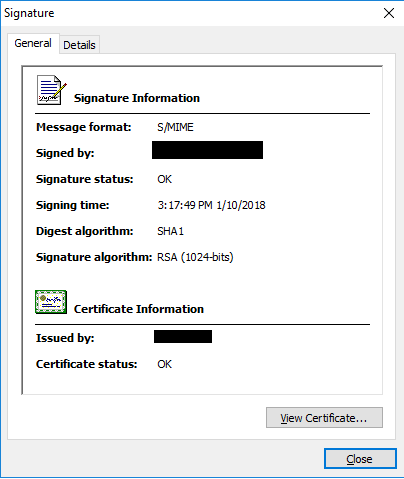
Pkcs #7 Signature
Maharishi regularly participated in intense meditation and introspection, which he claims brought him full enlightenment at the age of thirty-five. At the age of fifty, he closed his commercial ventures and devoted himself solely to spiritual service. However, he remained a 'householder', i.e. He did not break his family ties or take vows of renunciation, but rather lived in the indigenous tradition, maintaining family ties.Poems and books Shri Vethathiri Maharishi wrote over 3000 poems on philosophical subjects. Vethathiri maharishi exercise book pdf. After spending several years in various minor employment, he established a textile concern that grew to employ over 2,000 workers on a profit-sharing basis.
Oct 25, 2013 I am trying to implement signature verification for PDFs. It is a big topic so I am taking it one step at a time, first I am trying to actually return a positive in the case of a PDF I have signed myself, using all the default values with the current Acrobat — that should be SHA256 for the digest, and a PKCS7 detached signature.
In cryptography, PKCS stands for 'Public Key Cryptography Standards'. These are a group of public-key cryptography standards devised and published by RSA Security LLC, starting in the early 1990s. The company published the standards to promote the use of the cryptography techniques to which they had patents, such as the RSA algorithm, the Schnorr signature algorithm and several others. Though not industry standards (because the company retained control over them), some of the standards in recent years[when?] have begun to move into the 'standards-track' processes of relevant standards organizations such as the IETF and the PKIX working-group.
Solder the flying leads to the supply rails that the Lithium battery maintains (observing polarity) 4. Advantest r3132 service manual.
| Version | Name | Comments | |
|---|---|---|---|
| PKCS #1 | 2.2 | RSA Cryptography Standard[1] | See RFC 8017. Defines the mathematical properties and format of RSA public and private keys (ASN.1-encoded in clear-text), and the basic algorithms and encoding/padding schemes for performing RSA encryption, decryption, and producing and verifying signatures. |
| PKCS #2 | - | Withdrawn | No longer active as of 2010. Covered RSA encryption of message digests; subsequently merged into PKCS #1. |
| PKCS #3 | 1.4 | Diffie–Hellman Key Agreement Standard[2] | A cryptographic protocol that allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure communications channel. |
| PKCS #4 | - | Withdrawn | No longer active as of 2010. Covered RSA key syntax; subsequently merged into PKCS #1. |
| PKCS #5 | 2.1 | Password-based Encryption Standard[3] | See RFC 8018 and PBKDF2. |
| PKCS #6 | 1.5 | Extended-Certificate Syntax Standard[4] | Defines extensions to the old v1 X.509 certificate specification. Obsoleted by v3 of the same. |
| PKCS #7 | 1.5 | Cryptographic Message Syntax Standard[5] | See RFC 2315. Used to sign and/or encrypt messages under a PKI. Used also for certificate dissemination (for instance as a response to a PKCS #10 message). Formed the basis for S/MIME, which is as of 2010 based on RFC 5652, an updated Cryptographic Message Syntax Standard (CMS). Often used for single sign-on. |
| PKCS #8 | 1.2 | Private-Key Information Syntax Standard[6] | See RFC 5958. Used to carry private certificate keypairs (encrypted or unencrypted). |
| PKCS #9 | 2.0 | Selected Attribute Types[7] | See RFC 2985. Defines selected attribute types for use in PKCS #6 extended certificates, PKCS #7 digitally signed messages, PKCS #8 private-key information, and PKCS #10 certificate-signing requests. |
| PKCS #10 | 1.7 | Certification Request Standard[8] | See RFC 2986. Format of messages sent to a certification authority to request certification of a public key. See certificate signing request. |
| PKCS #11 | 2.40 | Cryptographic Token Interface[9] | Also known as 'Cryptoki'. An API defining a generic interface to cryptographic tokens (see also hardware security module). Often used in single sign-on, public-key cryptography and disk encryption[10] systems. RSA Security has turned over further development of the PKCS #11 standard to the OASIS PKCS 11 Technical Committee. |
| PKCS #12 | 1.1 | Personal Information Exchange Syntax Standard[11] | See RFC 7292. Defines a file format commonly used to store private keys with accompanying public key certificates, protected with a password-based symmetric key. PFX is a predecessor to PKCS #12. This container format can contain multiple embedded objects, such as multiple certificates. Usually protected/encrypted with a password. Usable as a format for the Java key store and to establish client authentication certificates in Mozilla Firefox. Usable by Apache Tomcat. |
| PKCS #13 | – | Elliptic Curve Cryptography Standard | (Apparently abandoned, only reference is a proposal from 1998.)[12] |
| PKCS #14 | – | Pseudo-random Number Generation | (Apparently abandoned, no documents exist.) |
| PKCS #15 | 1.1 | Cryptographic Token Information Format Standard[13] | Defines a standard allowing users of cryptographic tokens to identify themselves to applications, independent of the application's Cryptoki implementation (PKCS #11) or other API. RSA has relinquished IC-card-related parts of this standard to ISO/IEC 7816-15.[14] |
See also[edit]
References[edit]
- ^'PKCS #1: RSA Cryptography Standard'. RSA Laboratories.
- ^'PKCS #3: Diffie-Hellman Key Agreement Standard'. RSA Laboratories.
- ^'PKCS #5: Password-Based Cryptography Standard'. RSA Laboratories.
- ^'PKCS #6: Extended-Certificate Syntax Standard'. RSA Laboratories.
- ^'PKCS #7: Cryptographic Message Syntax Standard'. RSA Laboratories.
- ^'PKCS #8: Private-Key Information Syntax Standard'. RSA Laboratories.
- ^'PKCS #9: Selected Attribute Types'. RSA Laboratories.
- ^'PKCS #10: Certification Request Syntax Standard'. RSA Laboratories.
- ^'PKCS #11: Cryptographic Token Interface Standard'. RSA Laboratories.
- ^Security Token/Smartcard Support in FreeOTFE
- ^'PKCS #12: Personal Information Exchange Syntax Standard'. RSA Laboratories. Archived from the original on April 1, 2014.
- ^'PKCS #13: Elliptic Curve Cryptography Standard'. RSA Laboratories.
- ^'PKCS #15: Cryptographic Token Information Format Standard'. RSA Laboratories.
- ^ RSA Laboratories: 'PKCS #15: Cryptographic Token Information Format Standard'.
- General
- Jean-Sébastien Coron, Marc Joye, David Naccache, and Pascal Paillier (2000). 'New Attacks on PKCS #1 v1.5 Encryption'(PDF). EUROCRYPT. pp. 369–381.CS1 maint: multiple names: authors list (link)
External links[edit]
- About PKCS (appendix G from RFC 3447)
- OASIS PKCS 11 TC (technical committee home page)
The Cryptographic Message Syntax ( CMS) is the 's standard for protected messages. It can be used by cryptographic schemes and protocols to, or any form of digital data.CMS is based on the syntax of #7, which in turn is based on the standard.